Which of the Following Are Types of Data Security Safeguards
Which of the following are types of data security safeguards. Evaluation of the security controls already in place an accurate and thorough risk analysis and a series of documented solutions derived from a number of factors unique to each covered entity.

What Is Cyber Protection Definition Importance Types Cost Acronis
Which of the following is NOT typically used to categorize types of security safeguards.
. The law requires healthcare providers plans and other entities to uphold patient confidentiality privacy and security and calls for three types of. Or perform a secure deletion of all data using special methods that. Cyber security professionals should have an in-depth understanding of the following types of cyber security threats.
Encryption and authentication programs. Technical Safeguards are used to protect information through the use of which of the following. Why is protecting data important.
Malware is activated when a user clicks on a malicious link or attachment which leads to installing. A matrix of all of the Security Rule Standards and Implementation Specifications. Which of the following are types of data security safeguards.
Administrative safeguards for ePHI. This prevents unauthorized access from the outside by requiring identity-based authorization to access ePHI. This type of data security measures includes limiting both physical and digital access to critical systems and data.
The Department of Health Human Services. This is a summary of key elements of the Security Rule including who is covered what information is protected and what safeguards must be in place to ensure appropriate protection of electronic protected health information. The 3 categories for data protection safeguards are administrative physical and technical which are intended to ensure the confidentiality integrity and availability of data files and records.
Types of Data Security. The Three Safeguards of the Security Rule. January 18 2016 - When creating strong healthcare data security measures physical safeguards serve as a primary line of defense from potential threats.
When transmitting ePHI it should be encrypted. In an open computer network such as the internet HIPAA requires the use of _____. The ____Fill in the blank ____ is a unique ten-digit alphanumeric.
What are the different types of data protection safeguards. What are the types of data protection. These safeguards ensure employee compliance with the Security Rule.
The following terms describe the technical and organizational measures internal controls and information security routines that Accenture maintains to safeguard data provided by or on behalf of our clients in connection with a client service engagement Client Data. Administrative Standards are concerned with processes policies and procedures that will work to protect against a breach or unwanted disclosure of private information. Which of the following security management system standards is specific to the health care sector.
The Department of Health and Human Services considers the HIPAA security standards to be a maximum standard. What are Technical Safeguards. Here are three types of safeguards and examples of each that healthcare providers can use to protect against data breaches according to the authors of the article.
HIPAA SECURITY STANDARDS NOTE. Administrative physical and technical. Administrative safeguards are the policies and procedures that help protect against a breach.
Summary of the HIPAA Security Rule. Administrative Safeguards administrative actions and policies and procedures to manage the selection development implementation and maintenance of security measures to protect electronically protected health information and to manage the conduct of the covered entitys workforce in relation to the protection of that. Technical safeguards are used to protect information through the use of.
The department of health and human services considers the HIPAA security standards to be a maximum standard. The Security Rule requires implementation of three types of safeguards. Q3 Which of the following properties aim to generate a trail to identify the source and path of attack.
Technical safeguards pertain to the technology that protects personal health data such as firewalls encryption or data backups. Malware is malicious software such as spyware ransomware viruses and worms. Lets discuss the 3 categories of data protection safeguards to protect data including personal information and Protected Health Information or PHI under HIPAA.
Q1 Which of the following approaches generates a report with SWOT analysis. Secure data transmission. All of the above.
Technical data protection safeguards in a broader sense are the system controls and tools which are designed to protect data such as user authentication and passwords account lockout during extended inactivity periods and network intrusion prevention or detection controls. Because it is an overview of the Security Rule it does not address every detail of. Of the following types of conversations about patients the ones that constitutes a violation of patient privacy is.
There are three types of safeguards that you need to implement. The Security Rule defines technical safeguards in 164304 as the technology and the policy and procedures for its use that protect electronic As outlined in previous papers in this series the Security Rule is based on the fundamental concepts of flexibility scalability and technology neutrality. The HIPAA Security Rule contains what are referred to as three required standards of implementation.
Q2 Which of the following is a highly data-oriented review that provides independent inputs on SSA strategies. These security measures are intended to protect Client Data when in Accentures environments eg systems. Covered entities and BAs must comply with each of these.
7 Types of Cyber Security Threats. SSA Audits Interview Question-Answer.
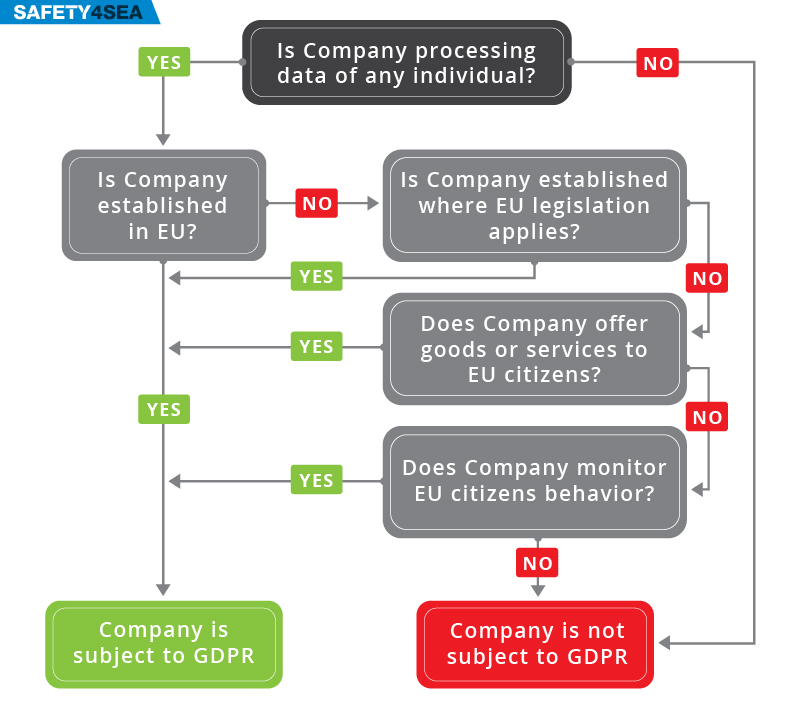
Cyber Security In The Eu Gdpr Framework Safety4sea
![]()
The Three States Of Data Guide Description And How To Secure Them

5 Things You Need To Know About Data Privacy Data Privacy Manager
No comments for "Which of the Following Are Types of Data Security Safeguards"
Post a Comment